The Australian Cyber Security Centre (ACSC) has recommended that all Australian organisations adopt the Essential 8 framework and aim to progress through the four Maturity Levels. But how does an organisation know where it is at and what needs to be implemented to progress from one level to the next?
What are the four Essential 8 Maturity Levels?
The Essential 8 is a set of eight controls designed to help organisations protect their networks and systems against cybersecurity threats.
The Maturity Levels of the Essential 8 refer to the degree to which an organisation has implemented each of the eight controls.
There are four maturity levels, as follows:
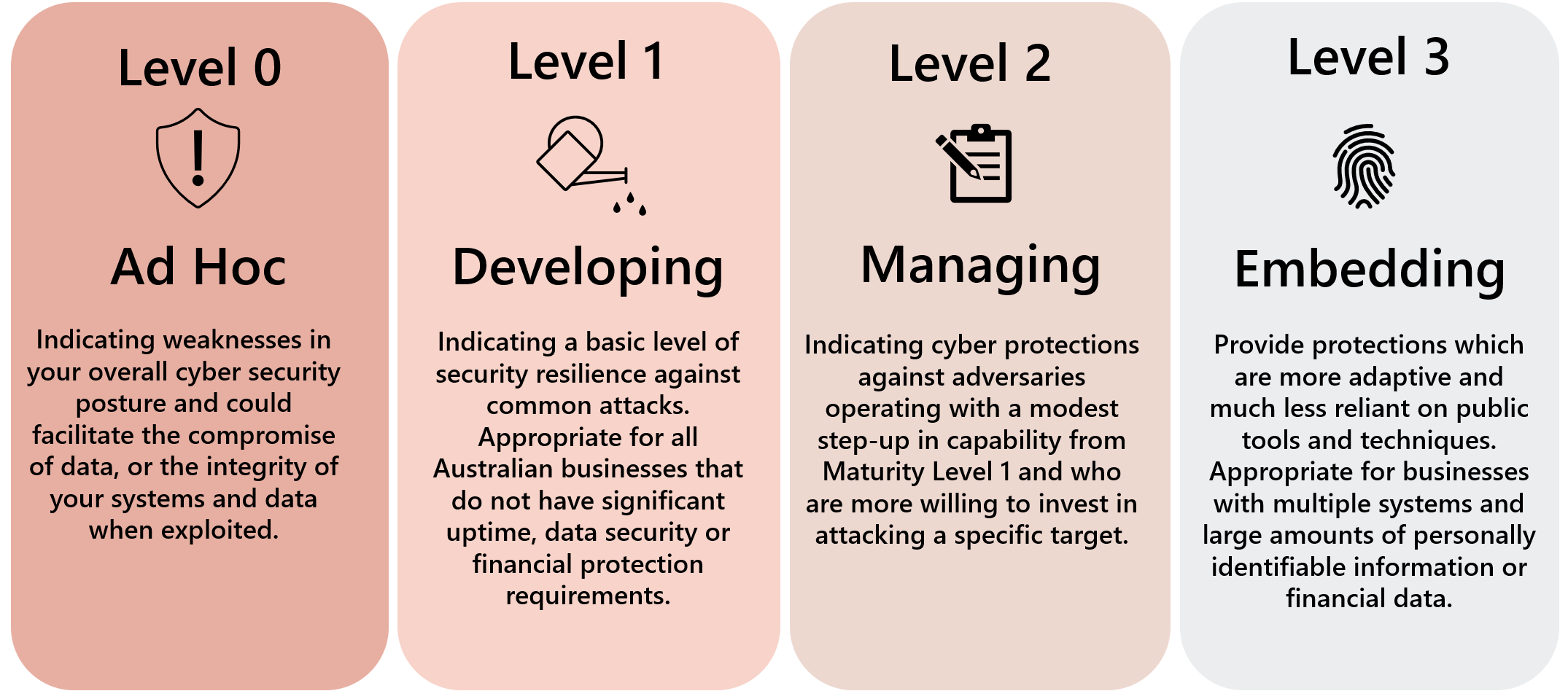
- Level 0 = Ad-Hoc
At this level, the organisation has no formal processes or procedures in place for implementing the Essential 8 strategies. Any implementation that occurs is ad-hoc and inconsistent.
- Level 1 = Developing
At this level, the organization has started to develop formal processes and procedures for implementing the Essential 8 strategies. Implementation is still inconsistent and may not be fully integrated into the organisation's operations.
- Level 2 = Managing
At this level, the organisation has established formal processes and procedures for implementing the Essential 8 strategies. Implementation is consistent across the organisation and is integrated into the organisation's operations.
- Level 3 = Embedding
At this level, the organisation has fully embedded the Essential 8 strategies into its operations. Implementation is consistent and ongoing, and the organisation regularly reviews and updates its processes and procedures to ensure they remain effective.
What Essential 8 Maturity Level should your organisation be aiming for?
You might think that all organisations should be aiming for the highest Maturity Level 3, but that may not be necessary or appropriate for many businesses.
The Essential 8 controls are designed to be adaptable and scalable to suit different organisational requirements and risk profiles.
Achieving Maturity Level 3 will be a worthwhile goal for many organisations, however, the maturity level that each organisation should aspire to will depend on its risk profile, the types of data being handled, and the potential impact of a cybersecurity breach on its operations.
The Essential 8 Maturity Level that an organisation should aim for depends on: its risk profile, the types of data it handles, and the potential impact of a cybersecurity breach on its operations.
a. Risk Profile
What is an organisation's risk profile? Organisations need to consider how attractive they would be as a target for cyber criminals, as this will increase the likelihood of being attacked.
Some of the key factors that can affect an organisation's cybersecurity risk profile include:
- Size and complexity of networks and systems
Larger networks potentially having more vulnerabilities and attracting a higher level of cyber threat than smaller organisations.
- Ability/Likelihood of paying a ransom
Some cybercriminals are content to take aim at sole operators and small businesses with the assumption these are more likely to quietly pay for their systems to be released, while others will target larger organisations with sensitive data they can sell if a ransom is not paid.
-
Industry sector
Different industry sectors may have different cybersecurity risks. For example, organisations in the financial sector may be at a higher risk of cyberattacks due to the sensitive nature of the data they handle.
-
Geographical location
The location of an organization can also impact its cybersecurity risk profile. Organisations in regions with a high incidence of cyberattacks may be at a higher risk than organisations in areas with lower cybercrime rates.
-
Internal policies and procedures
The policies and procedures an organisation has in place can also impact its cybersecurity risk profile. For example, an organisation with strong password policies and regular employee training on cybersecurity may be at a lower risk of cyberattacks than an organization with lax security policies.
-
Third-party relationships
The cybersecurity risks associated with third-party relationships should also be considered. Organisations that work with vendors, contractors, or other third-party service providers may be at a higher risk of cyberattacks due to the potential for those third parties to introduce vulnerabilities into the organisation's systems.
b. Data Sensitivity
The type of data an organisation handles will have a significant impact on its cybersecurity risk profile. Organisations that handle sensitive data such as financial information, medical records, or personally identifiable information (PII) will be at a higher risk of cyberattacks than organisations that handle less sensitive data.
c. Impact of a Cyber Breach
The impact of a cyber security incident on an organisation can vary from being inconvenient to being catastrophic.
Regardless of the level of breach, all cyber breaches will be expensive.
There may be an immediate and direct financial impact through the requirement to pay a ransom, loss of business while networks and systems are down, or the cost of bringing in experts to manage a breach.
There is also the broader financial impacts of reputational damage, loss of future business, legal action from parties whose data has been compromised, and potentially being fined by the OAIC or ASIC.
How should an organisation progress through the Essential 8 Maturity Levels?
The ACSC prioritises the implementation of all eight controls as a package. The eight controls have been designed to complement each other at each level, and to provide coverage across various types of cyber threats.
The ACSC recommends that organisations should fully achieve a maturity level across all eight controls, before moving onto a higher maturity level.
Where to start with the Essential 8 Maturity Levels
The first step is to assess the current state of your cyber security strategies against the Essential 8 framework.
This will require matching each Essential 8 Control and the associated benchmarks against your current environment.
In essence, you need to undertake a structured audit which assesses your existing compliance levels.
In completing an Audit it is important to consider the quality of the evidence that is being provided to demonstrate compliance.
In deciding whether the organisation is compliant, there should be evidence that can be quantified, proven, and documented.
"I'd love a dollar for every time we have been told pre-Audit that 'patching is done regularly and is up-to-date', only to find on inspection that patching has not been carried out for more than two years."
How to assess your organisation's Essential 8 Maturity level
There is no 'easy' way to assess your organisation's Essential 8 Maturity Level.
The assessment process understandably requires a thorough investigation of your environment to benchmark the current state against each Essential 8 Control.
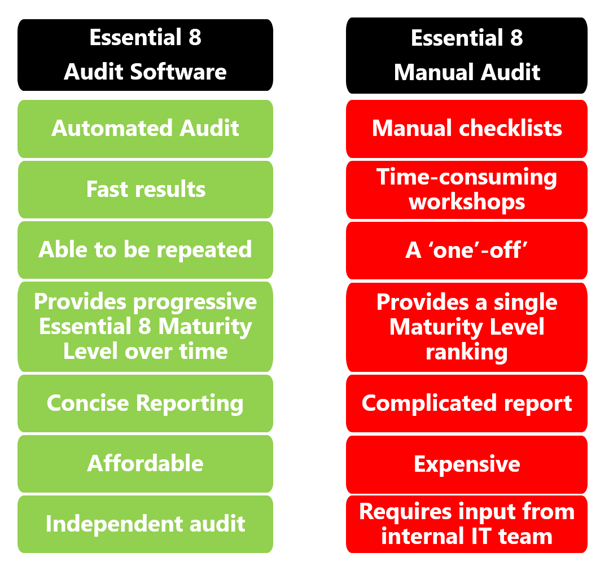
This audit process can be completed through manual checklists or through automated software.
Manual Essential 8 Audit
Many cyber security companies offer a labour-intensive Essential 8 Audit which comprises of manual checklists and workshops requiring significant input from an organisation's internal IT team.
These Audits often take months to complete and at the conclusion an organisation is presented with a comprehensive assessment report, which may or may not provide a remediation roadmap.
It is not uncommon for these Audits to be priced around AUD$20,000 or more depending on the size and complexity of the networks and systems.
Automated Essential 8 Audit Software
As an alternative to a manual audit, some organisations are utilising enterprise-grade audit software to carry out an independent audit which can be completed in hours and is able to be repeated as required.
We are biased at MobileCorp because we have been through the automated software Essential 8 Audit journey. As a mid-market company, we are now Maturity Level 3 compliant.
We appreciate the benefits of being able to run the audit software through our environment monthly or more often should we wish to do so.
The audit has identified our gaps, informed our remediation roadmap, and shifted us progressively to Maturity Level 3.
It is also significantly less expensive than a manual audit, and took up less of our IT team's time.
Essential 8 Audit is not a 'one-off'
Being compliant with the Essential 8 framework is not a one-off exercise, it is a continuous process.
The E8 controls require regular specific activity undertaken continuous to remain compliant.
It is not ideal to complete an Essential 8 Audit as a massive exercise at the start of this journey, and then not audit again.
It makes sense to have a means of auditing that is repeatable, allows organisations to to understand their E8 risk profile at all times, and that provides an evidential record of continuous improvement.
What is MobileCorp's Essential 8 Audit as-a-Service?
MobileCorp's Essential 8 Audit-as-a-Service utilises automated audit software that provides
- fortnightly Essential 8 Audit of your environment
- visibility of Essential 8 compliance at-a-glance for business and IT leaders
- detailed Gap Analysis Report for remediation activity
- Compliance Reporting for each control to meet governance requirements
- benchmarked monthly ACSC Maturity Level ranking
- No data privacy concerns. All data remains stored in your environment
- A MobileCorp account manager to present your reports



What is required at each Essential 8 Maturity Level?
In order to understand how to progress your Essential 8 Maturity Level, you need to understand the requirements of each level.
The tables below summarise the varying compliance requirements at each Maturity Level for each Essential 8 control.
Controls to Prevent Attacks
APPLICATION CONTROL |
||
Level 1 |
Level 2 |
Level 3 |
|
The execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications and control panel applets is prevented on workstations from within standard user profiles and temporary folders used by the operating system, web browsers and email clients. |
Application control is implemented on workstations and internet-facing servers. |
Application control is implemented on workstations and servers. |
|
Application control restricts the execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications and control panel applets to an organisation-approved set. |
Application control restricts the execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications, control panel applets and drivers to an organisation-approved set. |
|
|
Allowed and blocked execution events on workstations and internet-facing servers are logged. |
Microsoft’s ‘recommended block rules’ are implemented. |
|
|
|
Microsoft’s ‘recommended driver block rules’ are implemented. |
|
|
|
Application control rulesets are validated on an annual or more frequent basis. |
|
|
|
Allowed and blocked execution events on workstations and are centrally logged. |
|
|
|
Event logs are protected from unauthorised modification and deletion. |
|
|
|
Event logs are monitored for signs of compromise and actioned when any signs of compromise are detected. |
|
PATCH APPLICATIONS |
||
Level 1 |
Level 2 |
Level 3 |
|
An automated method of asset discovery is used at least fortnightly to support the detection of assets for subsequent vulnerability scanning activities.. |
A vulnerability scanner is used at least weekly to identify missing patches or updates for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products. |
Patches, updates or vendor mitigations for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products are applied within two weeks of release, or within 48 hours if an exploit exists. |
|
A vulnerability scanner with an up-to-date vulnerability database is used for vulnerability scanning activities. |
A vulnerability scanner is used at least fortnightly to identify missing patches or updates for security vulnerabilities in other applications. |
Applications that are no longer supported by vendors are removed. |
|
A vulnerability scanner is used at least daily to identify missing patches or updates for security vulnerabilities in internet-facing services. |
Patches, updates or vendor mitigations for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products are applied within wo weeks f release. |
|
|
A vulnerability scanner is used at least fortnightly to identify missing patches or updates for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products. |
Patches, updates or vendor mitigations for security vulnerabilities in other applications are applied within one month of release. |
|
|
Patches, updates or vendor mitigations for security vulnerabilities in internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists. |
|
|
|
Patches, updates or vendor mitigations for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products are applied within one month of release. |
|
|
|
Internet-facing services, office productivity suites, web browsers and their extensions, email clients, PDF software, Adobe Flash Player, and security products that are no longer supported by vendors are removed. |
|
|
CONFIGURE MICROSOFT OFFICE MACROS |
||
Level 1 |
Level 2 |
Level 3 |
|
Microsoft Office macros are disabled for users that do not have a demonstrated business requirement. |
Microsoft Office macros are blocked from making Win32 API calls. |
Only Microsoft Office macros running from within a sandboxed environment, a Trusted Location or that are digitally signed by a trusted publisher are allowed to execute. |
|
Microsoft Office macros in files originating from the internet are blocked. |
Allowed and blocked Microsoft Office macro execution events are logged. |
Only privileged users responsible for validating that Microsoft Office macros are free of malicious code can write to and modify content within Trusted Locations. |
|
Microsoft Office macro antivirus scanning is enabled. |
Microsoft Office macros digitally signed by an untrusted publisher cannot be enabled via the Message Bar or Backstage View. |
|
|
Microsoft Office macro security settings cannot be changed by users. |
Microsoft Office’s list of trusted publishers is validated on an annual or more frequent basis. |
|
|
|
Allowed and blocked Microsoft Office macro execution events are centrally logged. |
|
|
|
Event logs are protected from unauthorised modification and deletion. |
|
|
|
Event logs are monitored for signs of compromise and actioned when any signs of compromise are detected. |
|
USER APPLICATION HARDENING |
||
Level 1 |
Level 2 |
Level 3 |
|
Web browsers do not process Java from the internet. |
Microsoft Office is blocked from creating child processes. |
Internet Explorer 11is disabled or removed. |
|
Web browsers do not process web advertisements from the internet. |
Microsoft Office is blocked from creating executable content. |
.NET Framework 3.5 (includes .NET 2.0 and 3.0) is disabled or removed. |
|
Internet Explorer 11 does not process content from the internet. |
Microsoft Office is blocked from injecting code into other processes. |
Windows PowerShell 2.0 is disabled or removed. |
|
Web browser security settings cannot be changed by users. |
Microsoft Office is configured to prevent activation of OLE packages. |
PowerShell is configured to use Constrained Language Mode. |
|
Microsoft Office security settings cannot be changed by users. |
Blocked PowerShell script execution events are centrally logged. |
|
| PDF software is blocked from creating child processes. | Event logs are protected from unauthorised modification and deletion. | |
| PDF software security settings cannot be changed by users. | Event logs are monitored for signs of compromise and actioned when any signs of compromise are detected. | |
|
ACSC or vendor hardening guidance for web browsers, Microsoft Office and PDF software is implemented. |
||
|
Blocked PowerShell script execution events are logged. |
||
Controls to limit the extent of Attacks
PATCH OPERATING SYSTEMS |
||
Level 1 |
Level 2 |
Level 3 |
|
An automated method of asset discovery is used at least fortnightly to support the detection of assets for subsequent vulnerability scanning activities. |
A vulnerability scanner is used at least weekly to identify missing patches or updates for security vulnerabilities in operating systems of workstations, servers and network devices. |
Patches, updates or vendor mitigations for security vulnerabilities in operating systems of workstations, servers and network devices are applied within two weeks of release, or within 48 hours if an exploit exists. |
|
A vulnerability scanner with an up-to-date vulnerability database is used for vulnerability scanning activities. |
Patches, updates or vendor mitigations for security vulnerabilities in operating systems of workstations, servers and network devices are applied within two weeks of release. |
The latest release, or the previous release, of operating systems are used. |
|
A vulnerability scanner is used at least daily to identify missing patches or updates for security vulnerabilities in operating systems of internet-facing services. |
|
|
|
A vulnerability scanner is used at least fortnightly to identify missing patches or updates for security vulnerabilities in operating systems of workstations, servers and network devices. |
|
|
|
Patches, updates or vendor mitigations for security vulnerabilities in operating systems of internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists. |
|
|
|
Patches, updates or vendor mitigations for security vulnerabilities in operating systems of workstations, servers and network devices are applied within one month of release. |
|
|
|
Operating systems that are no longer supported by vendors are replaced. |
|
|
MULTI-FACTOR AUTHENTICATION |
||
Level 1 |
Level 2 |
Level 3 |
|
Multi-factor authentication is used by an organisation’s users if they authenticate to their organisation’s internet-facing services. |
Multi-factor authentication is used to authenticate privileged users of systems. |
Multi-factor authentication is used to authenticate users accessing important data repositories. |
|
Multi-factor authentication is used by an organisation’s users if they authenticate to third-party internet-facing services that process, store or communicate their organisation’s sensitive data. |
Multi-factor authentication uses either: something users have and something users know, or something users have that is unlocked by something users know or are. |
Multi-factor authentication is phishing-resistant and uses either: something users have and something users know, or something users have that is unlocked by something users know or are. |
|
Multi-factor authentication (where available) is used by an organisation’s users if they authenticate to third-party internet-facing services that process, store or communicate their organisation’s non-sensitive data. |
Successful and unsuccessful multi-factor authentication events are logged. |
Successful and unsuccessful multi-factor authentication events are centrally logged. |
|
Multi-factor authentication is enabled by default for non-organisational users (but users can choose to opt out) if they authenticate to an organisation’s internet-facing services. |
|
Event logs are protected from unauthorised modification and deletion. |
|
|
|
Event logs are monitored for signs of compromise and actioned when any signs of compromise are detected. |
RESTRICT ADMINISTRATIVE PRIVILEGES |
||
Level 1 |
Level 2 |
Level 3 |
|
Requests for privileged access to systems and applications are validated when first requested. |
Privileged access to systems and applications is automatically disabled after 12 months unless revalidated. |
Privileged access to systems and applications is limited to only what is required for users and services to undertake their duties. |
|
Privileged accounts (excluding privileged service accounts) are prevented from accessing the internet, email and web services. |
Privileged access to systems and applications is automatically disabled after 45 days of inactivity. |
Privileged accounts are pevented from accessing the internet, email and web services. |
|
Privileged users use separate privileged and unprivileged operating environments. |
Privileged operating environments are not virtualised within unprivileged operating environments. |
Just-in-time administration is used for administering systems and applications. |
|
Unprivileged accounts cannot logon to privileged operating environments. |
Administrative activities are conducted through jump servers. |
Windows Defender Credential Guard and Windows Defender Remote Credential Guard are enabled. |
|
Privileged accounts (excluding local administrator accounts) cannot logon to unprivileged operating environments. |
Credentials for local administrator accounts and service accounts are long, unique, unpredictable and managed. |
Privileged access events are logged. |
|
|
Privileged access events are logged. |
Privileged account and group management events are centrally logged. |
|
|
Privileged account and group management events are logged. |
Event logs are protected from unauthorised modification and deletion. |
|
|
|
Event logs are monitored for signs of compromise and actioned when any signs of compromise are detected. |
|
|
|
Just-in-time administration is used for administering systems and applications. |
Controls to Recover Data and System Availability
REGULAR BACKUPS |
||
Level 1 |
Level 2 |
Level 3 |
|
Backups of important data, software and configuration settings are performed and retained with a frequency and retention timeframe in accordance with business continuity requirements. |
Privileged accounts (excluding backup administrator accounts) cannot access backups belonging to other accounts. |
Unprivileged accounts cannot access backups belonging to other accounts, nor their own accounts. |
|
Backups of important data, software and configuration settings are synchronised to enable restoration to a common point in time. |
Privileged accounts (excluding backup administrator accounts) are prevented from modifying and deleting backups. |
Privileged accounts (excluding backup administrator accounts) cannot access backups belonging to other accounts, nor their own accounts. |
|
Backups of important data, software and configuration settings are retained in a secure and resilient manner. |
|
Privileged accounts (including backup administrator accounts) are prevented from modifying and deleting backups during their retention period. |
|
Restoration of important data, software and configuration settings from backups to a common point in time is tested as part of disaster recovery exercises. |
|
|
|
Unprivileged accounts cannot access backups belonging to other accounts. |
|
|
|
Unprivileged accounts are prevented from modifying and deleting backups. |
|
|
What are the next steps?
- Research your options. The ACSC website is a great place to start.
- Engage with vendors who offer the various Essential 8 Audit services - manual and automated - and obtain a full understanding of the process, the internal input required, security protocols, timeframe, outcomes and cost.
If you are interested in learning more about MobileCorp's Essential 8 Audit and Remediation services, reach out to:
Jim Joannou

About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. We provide Essential 8 Cyber Security as a Service, Managed Mobility Services, Enterprise Mobility Management, Complex Data and IP Networks, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and we are a Telstra Platinum Partner.
MobileCorp Managed Services Michelle Lewis 12 Apr 2023
Related Posts
Popular Tags
- Mobility (81)
- Mobile Devices (79)
- Telstra (66)
- 5G (64)
- MobileCorp Managed Services (55)
- Mobile Network (34)
- Networks (34)
- Cradlepoint (32)
- Apple (29)
- MobileCorp (29)
- iPhone (25)
- Remote Working (23)
- Network (17)
- Covid-19 (16)
- Mobile Security (15)
- Wireless WAN (15)
- Cyber Security (14)
- UEM (14)
- MDM (11)
- Mobile Expense Management (10)
- Mobile Device Management (9)
- TEMs (9)
- Mobile Device Lifecycle (8)
- Cloud (7)
- Unified Comms (7)
- Unified Communications (7)
- Wandera (7)
- Android (6)
- Sustainability (6)
- Data Networks (5)
- Network Security (5)
- Samsung (5)
- Security (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Blog (3)
- IT Services (3)
- Microsoft (3)
- Data (2)
- Government (2)
- Microsoft 365 & Teams (2)
- Retail (2)
- nbn (2)
- webinar (2)
- 4G (1)
- DAS (1)
- EMM (1)
- Emerging Technologies (1)
- Hosted Telephony (1)
- Managed Desktops (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- WWAN (1)
- video (1)