- Home Page
- Data Networks
- Network Security
- Next Gen Firewalls
Next-Generation Firewalls
My message for companies that think they haven’t been attacked is: “you’re not looking hard enough!”
Enquire Now



What are Next-Generation Firewalls?
Firewalls are a standard security tool for most companies, but in today’s changing threat landscape, next-generation firewalls are the only firewalls that can provide proper protection.
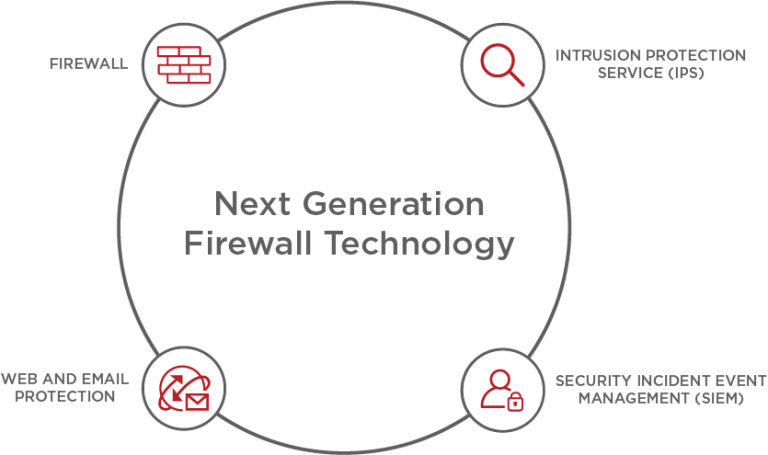
As the name suggests, Next-Generation Firewalls are a more powerful advanced version of the traditional firewall. They offer all the same benefits, plus a whole range of additional features to address applications in the cloud, and to block more potential threats.
Why Next-Generation firewalls?
In 2023, a new generation of users, applications, and security threats pose risks to the enterprise wireless network.
Traditional firewalls are not strong enough to provide complete application visibility and control. Having a next gen firewall in place ensures an enterprise is ready to securely integrate mobile users and cloud computing.
As the name suggests, next generation firewalls are a more powerful advanced version of the traditional firewall. They offer all the same benefits, plus a whole range of additional features to address applications in the cloud, and to block more potential threats.
Like regular firewalls, NGFW use both static and dynamic packet filtering and VPN support to ensure that all connections between the network, internet, and firewall are valid and secure. The most obvious difference between the two is an NGFW’s ability to filter packets based on applications.
Next Gen firewalls have extensive control and visibility of applications by using analysis and signature matching. They can use whitelists or a signature-based IPS to distinguish between safe applications and unwanted ones, which are then identified using SSL decryption. Unlike most traditional firewalls, NGFWs also include a path through which future updates will be received.
The difference between a next-generation firewall and earlier firewalls is like the difference between a smartphone and an early mobile phone. Both have some features in common – voice calls, voicemail – but that’s where it ends.

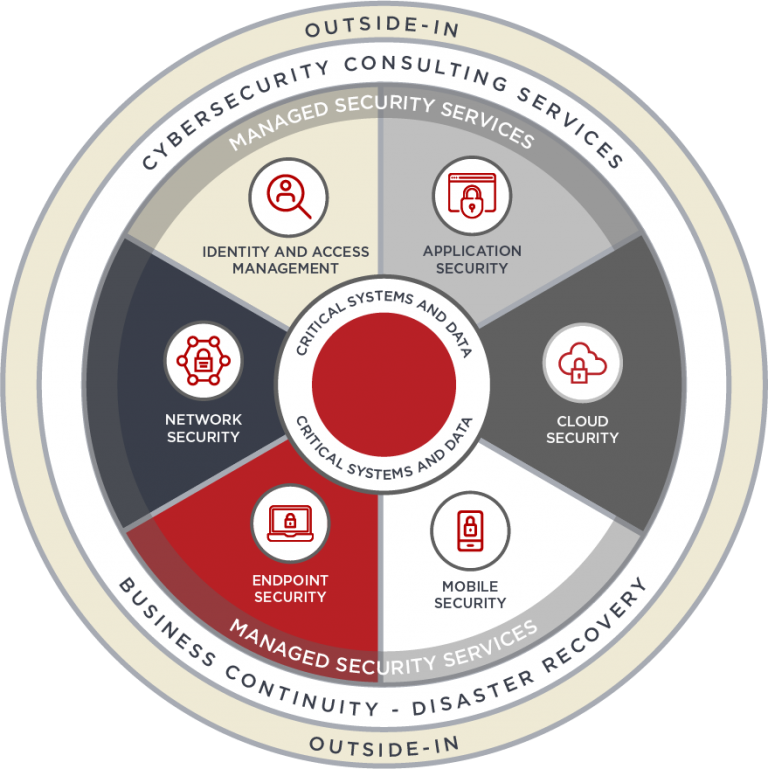
MobileCorp Next-Generation Firewall professional service
MobileCorp offers expert advice about the options for firewall security. This may be as part of a wider network security review or refresh, or as a stand-alone upgrade.
Some of the feature sets that MobileCorp can assist with from both a mobility and fixed network perspective include:
- Geolocation
- DS/IPS
- Antivirus/anti-malware
- Sandboxing
- Web proxy and URL checking
- Reverse proxy
- Web application firewall
- Load balancing
Geolocation
Geolocation is the ability to associate IP addresses with physical locations. Because IP address allocations change rather frequently, geolocation requires intermittent updates to remain current.
IDS/IPS
Intrusion detection or prevention systems look at the contents of packets going through the firewall and try to spot things that look like attacks. Because new attacks appear constantly, IDS/IPS devices tend to become less useful over time unless their signatures are regularly updated.
Anti-virus | Anti-malware
As files are uploaded or downloaded, they pass through the firewall and it can do a basic examination. In most cases, this will be signature-based analysis, looking at checksums and scanning inside the file for patterns of bytes that have been seen in known malware in the past. This feature obviously requires that files are not encrypted and the firewall has a recently updated set of signatures.
Sandboxing
A better form of malware scanning is called a sandbox. This is essentially a virtual machine (VM) running a common target operating system such as Windows. The firewall intercepts the file download and sends it over to the sandbox VM where it’s “detonated”, meaning the VM tries to run the file as if it were the target computer. The sandbox then looks for common types of malicious behaviour such as connecting to command and control (C&C) networks.
In some cases, the sandbox is a separate physical box sitting at the network edge. In other cases, it’s a cloud service. It tends to be less effective to put a sandbox inside the firewall because the sandbox requires so many memory and CPU resources to run.
Web Proxy and URL checking
Worth URL checkers and web proxies can be cloud services, or they can use separate physical boxes on-site. Typically, both types of services will provide detection for a wide range of content types, not just malware. For example, they can be used to enforce appropriate-use policies against adult sites, gaming, video streaming, and so forth.
Reverse Proxy
One of the principal benefits of a reverse proxy is that it can sit in front of a relatively insecure web server and ensure attackers can’t hit it directly.
A reverse proxy can also help mitigate certain types of denial of service attacks, a service model that’s particularly effective if the reverse proxy is a cloud service.
Web Application Firewall
A web application firewall (WAF) is a more sophisticated version of a reverse proxy. A WAF typically look for things like attempted buffer overflow attacks on input fields, SQL injection attacks, cross-site scripting, and so forth. It also tries to detect any attempts to exploit known vulnerabilities in web server software.
Load Balancing
Some next-gen firewalls include a load balancer feature. This can be applied in different ways for data centre and remote branch implementations.
Next-Generation v Traditional Firewalls
Next gen firewalls offer many features which are an upgrade on traditional firewalls. These include:
Application Identification
Application identification answers the question, ‘what sort of traffic is allowed?’
It uses multiple identification mechanisms to determine the exact identity of applications crossing the network. As the applications are identified through a multi-factor approach, the policy check determines how to treat the applications and related functions.
Accurate traffic classification is the core of any firewall.
Application Control
Application control is as critical as identification. Next Gen firewalls provide granular application usage control policies such as:
- allowing or denying
- allowing certain application functions and applying traffic shaping,
- decrypt and inspecting,
- allowing for certain users and groups.
It increases productivity, prevents data leakage and protects against application-borne malware.
Malware Threat Prevention
In order to prevent threats effectively, the network needs to first reduce the avenues of attack by controlling which applications run on it. Then, a firewall needs to scan ‘allowed’ application traffic for threats more broadly, while not limiting them to a strict definition of a particular type of threat (e.g. “virus” or “exploit”). Two security features of next gen firewalls are:
- Intrusion prevention system (IPS): An intrusion prevention system actively detects and blocks attacks. This is like having a security guard who actively patrols a building, instead of one who just sits next to the front entrance.
- Deep packet inspection (DPI): Older firewalls typically inspect only the headers* of the data packets passing through. NGFWs inspect both data packet headers and the packet payload, in order to better detect malware and other kinds of malicious traffic. This is somewhat like a security checkpoint where the security officers actually inspect the contents of a person’s luggage, instead of just having that person tell the officers what items are in their luggage.
Directory Integration
User directories allow an organisation’s internal teams to track the privileges and permissions each user has. Some NGFWs can filter network traffic or applications based on these internal user directories. If a user does not have permission to access a certain application, then that application is blocked for that user by the firewall, even if the application isn’t identified as malicious.
Encrypted Traffic Inspection
Some next gen firewalls can actually decrypt and analyse traffic that is encrypted with SSL/TLS. A firewall is able to do this by acting as a proxy for the TLS process. All traffic to and from the website is decrypted by the firewall, analysed, and encrypted again. From a user’s point of view, this proxying is virtually seamless, and they can interact with secure HTTPS websites like normal.
Single Security Option
Next gen firewalls can be a low-cost option for companies looking to improve their basic security because they can incorporate the work of antiviruses, firewalls, and other security applications into one solution.

Should I opt for Cloud or On-Premise firewalls?
Cloud benefits
For companies who are comfortable with their data being hosted in the cloud, there can be significant financial and security benefits in a cloud-based firewall solution.
Remote Employee Support
Employees are increasingly reliant on cloud-based applications and cloud-based access to the network from remote locations. Cloud-based next gen firewalls are attuned to this generation of user behaviour and provide the level of security support to match.
OpEx expense
The cost shifts from a capital expense to an operational expense which has a number of financial benefits.
Pay-As-You-Go
Organisations only pay for what is used, and don’t have to purchase more firewall appliance capability than usually needed in order to be prepared for the busiest time periods.
Zero-Day Threat Fix
No need to download and install updates to meet emerging threats. The service provider keeps the firewall up to date and configured properly.
Guarding Against DDoS Attacks
The cloud provider has bandwidth to repel attacks at gigabit or terabit scale. An attack will be directed and blocked by the bandwidth-rich vendor servers and should not affect an individual organisation’s Internet connection.
On-Premise benefits
There are some businesses that will not consider a cloud-based firewall because critical importance is placed on retaining all data in-house rather than allowing it – even encrypted – to leave the premises.
The latency, delays and risks associated with running confidential data to/from a cloud provider are greater than some organisations are willing to tolerate.
Less Risk
Data does not leave the network eliminating the risk of sending it to the Cloud
Retain Control over Data
An on-premise solution provides businesses with control over all the data, managed and handled by their own dedicated IT staff.
2 layer defence
On-premise solutions can provide significantly better threat protection than is available in cloud deployments.
Most modern on-premise solutions automatically update themselves with the latest protection and often leverage the cloud to provide a second layer of defence against various attacks.
While it is true that some things are easier to administer through the cloud, security is not one of them. Some services, such as distributed denial-of-service protection, can benefit from cloud deployments, but this is also something that could better handled at the ISP level.
Data Sensitive Industries
Some industries lend themselves to a preference for on-premise security solutions.
The military will likely always opt for closed on-premise networks because they cannot risk sensitive data related to national security being intercepted and/or modified through a cloud-based solution.
Financial institutions such as banks and credit card agencies will also likely always opt for closed on-premise networks because they cannot risk sensitive data related to financial records, accounting and money transfers being intercepted and/or modified in the cloud.
Being on-premise makes it easier to integrate and tailor features tightly to the needs of a particular industry. This includes the ability to perform network forensics quickly and easily.
What about ‘Firewall as a Service’?
Another option to consider is Firewall as a Service. This could have significant benefits, especially for small to medium businesses with limited internal IT security resource. Benefits include:
- Pay for what is used – avoid buying firewall appliance capacity to cover busiest time periods, which may be an occasional occurrence. Pay as you Go model means the business only pays for the capacity in use.
- Instant response to new threats – new zero-day threats and fixes, can be applied instantly by the service provider. This negates the need to download and install updates.
- Guard against DDoS attacks – guarding against distributed denial-of-service (DDoS) attacks can be difficult no matter how much bandwidth a business has. Going cloud-scale can help, because the cloud provider has bandwidth to repel attacks at gigabit or terabit scale. Any attack will be directed and blocked by the bandwidth-rich FWaaS servers and should not affect the business’ Internet connection.
Our Tech Partners
Leaders we are proud to partner with.





















From the Blog
Cyber Security
Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now