- Home Page
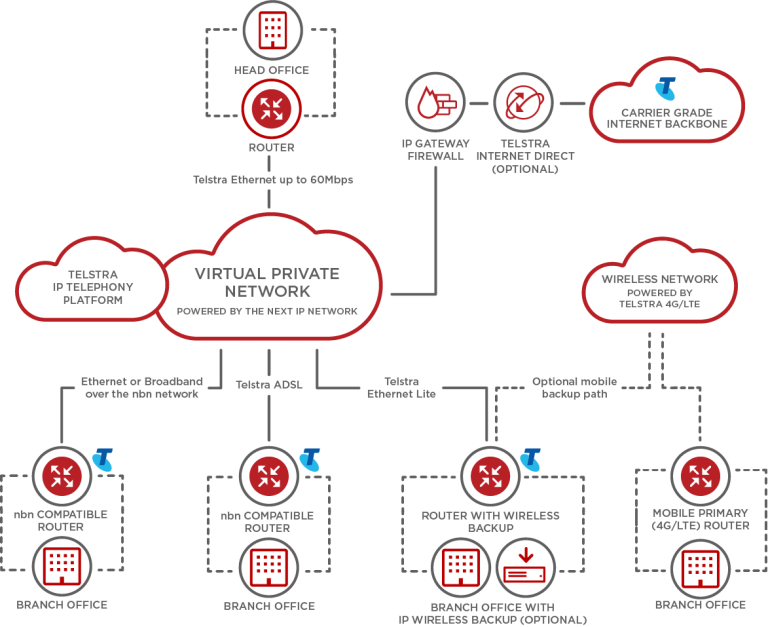
- Managed ICT & IT Services
- Network & Infrastructure Services
- Proactive Network Monitoring
Proactive Network Monitoring
Peace-of-mind and confidence - two priceless outcomes of vigilance
Enquire Now




What is Proactive Network Monitoring?
Monitoring is a critical IT process. All networking components such as routers, switches, firewalls, servers, and VMs should be monitored for fault and performance; and evaluated continuously to maintain and optimise availability and to be vigilant against intrusion.
Key benefits of Network Monitoring
The benefits of proactively monitoring the network are:
- Risk mitigation and prevention of downtime or failure
Efficient proactive monitoring can prevent network downtime or failures by allowing early detection and intervention. Some issues that would be captured by monitoring include if something stops responding, a server fails or disk space is running low.
- Quick restoration
Continuous monitoring identifies the fault and eliminates the investigation phase of diagnosis. This will reduce the time the fault may impact on end users.
- Trend analysis
Monitoring can track trends in the performance of the network. When problems occur sporadically or at peak times, they can be difficult to detect but network monitoring can analyse performance patterns.
- Succession planning
With network monitoring there is visibility of devices running near their limit, allowing the ability to plan ahead for upgrades or replacement. Detailed monitoring reporting can inform and justify the business case for expenditure.
- Save time and money
Eliminate investigation time, speed diagnosis of issues, and proactively replace before disruption. All these elements protect productivity and profitability, and allow time to be spent on the core business.
MobileCorp Network Monitoring managed service
MobileCorp delivers peace of mind and confidence that the network is being proactively monitored for potential threats and optimal performance.
Customer internal IT resources can be freed from the responsibility of being 24/7 responsive to a network threat by outsourcing network monitoring to MobileCorp.
MobileCorp’s network monitoring managed service provides:
- Remote monitoring software installation to allow remote monitoring of network devices, including switches, routers, and firewalls.
- Alert notifications about device availability, performance, security, and backup status.
- Performance health checks of hardware and software on workstations, servers, and network devices across multiple work locations.
- Security monitoring including antivirus scanning statuses, errors in event logs.
- Background maintenance to fix issues without disrupting end users or causing downtime, by using remote command lines and custom scripts, and by managing system processes and services.
- Scheduled maintenance windows to run during off hours to prevent disruption of employee productivity or false downtime alarms.
- Automation and bulk actions utilised to standardise checks, rules, and tasks across sites, servers, and workstations.
- Response policy enacted to resolve or remediate an issue identified by monitoring.
Setting up MobileCorp’s Network Monitoring Service
MobileCorp will work alongside customers to define the parameters of the design, build, and maintenance requirements for the network monitoring managed service.
Step 1. Prioritising The Essentials
In effective network monitoring, the first step is to identify the devices and the related performance metrics to be monitored. The second step is determining the monitoring interval.
Devices like desktops and printers are not critical and do not require frequent monitoring whereas servers, routers and switches perform business critical tasks but at the same time have specific parameters that can be selectively monitored.
Step 2. Setting The Monitoring Interval
The monitoring interval determines the frequency at which the network devices and its related metrics are polled to identify performance and availability status.
The interval depends on the type of network device or parameter being monitored. Availability status of devices have to be monitored most often, preferably every minute. CPU and memory stats can be monitored once in every 5 minutes.
The monitoring interval for other metrics like disk utilisation can be extended and it may be sufficient to poll every 15 minutes.
Monitoring every device at the least interval only adds unnecessary load to the network.
Step 3. Adopting a Non-Bandwidth Consuming Protocol 
When monitoring a network and its devices, a good practice is to adopt a secure and non-bandwidth consuming network management protocol to minimise the impact it has on network performance.
Most of the network devices and Linux servers support SNMP (Simple Network Management Protocol) and CLI protocols and Windows devices support WMI protocol.
SNMP is one of the widely accepted protocols to manage and monitor network elements.
Most of the network elements come bundled with a SNMP agent. They just need to be enabled and configured to communicate with the network management system (NMS).
Allowing SNMP read-write access gives one complete control over the device.
Using SNMP, MobileCorp can replace the entire configuration of the device.
A network monitoring system also allows MobileCorp to take charge of the network by setting SNMP read/write privileges and restricting control for other users.
Step 4. Setting Threshold Alerts
The key challenge in network monitoring is to identify performance bottlenecks proactively. This is where thresholds play a major role in network monitoring.
Threshold limits vary from device to device based on the business use case. Configuring thresholds helps in proactively monitoring the resources and services running on servers and network devices. Each device can have an interval or threshold value set based on user preference and need.
Multi-level threshold can assist in classifying and breaking down any fault encountered.
Utilising thresholds means alerts can be raised before the device goes down or reaches critical condition.
Step 5. Delivering High Availability
High availability refers to the continuous availability of a monitoring system. Every single network incident – device sickness, unhealthy bandwidth levels, DoS attacks – should immediately stimulate an alert so that countermeasures can be taken immediately.
Step 6. Setting Up Dashboards 
A network dashboard should provide an at-a-glance overview of the current status of the network, with critical metrics from routers, switches, firewalls, servers, services, application, URLs, printer, UPS and other infrastructure devices.
Step 7. Preparing For Failover 
What happens when the network monitoring solution is running on a server that crashes or loses network connection? Set up an alerted and also have the situation automatically remedied using a back-up/stand-by of another twin network monitor application installation.
Failover and fail-back functionality ensure an always-monitored network environment by utilising a secondary standby server. If a failure occurs in the primary server, the secondary server is available to take over and the database is secure. This ensures a hundred percent network and device uptime.
Step 8: Setting Granular Roles and Permissions 
MobileCorp network specialists will work with the customer to set strong rules around accessibility and to determine the process which will be followed for each incident detected by the monitoring service. These may or may not involve MobileCorp taking action to resolve or remediate an issue, dependent on the customer.

Our Tech Partners
Leaders we are proud to partner with.





















Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now