- Home Page
- Managed ICT & IT Services
- Security Services
- MobileCorp Security Management
Security Management
Protection or Detect-Respond - which security model ?
Enquire Now



Prevention or Detect-Respond model?
The world has adopted a detect-and-respond model that causes security teams to chase down problems and deal with them, often requiring re-imaging of machines or restoring from backups.
Shifting to a more balanced approach with the addition of ‘prevention-first’ strategies can head off some threats before they manifest. It allows security teams to reduce risk while vastly improving the end-user’s satisfaction.
Gartner: more balanced response is required
Global research consultancy, Gartner, has reported that organisations are now shifting to invest in security tools that are more sensitive and are focusing on a balance between response and detection versus prevention.
This rise in more sophisticated alerts and tools has led to an increased need to centralise and optimise operations.
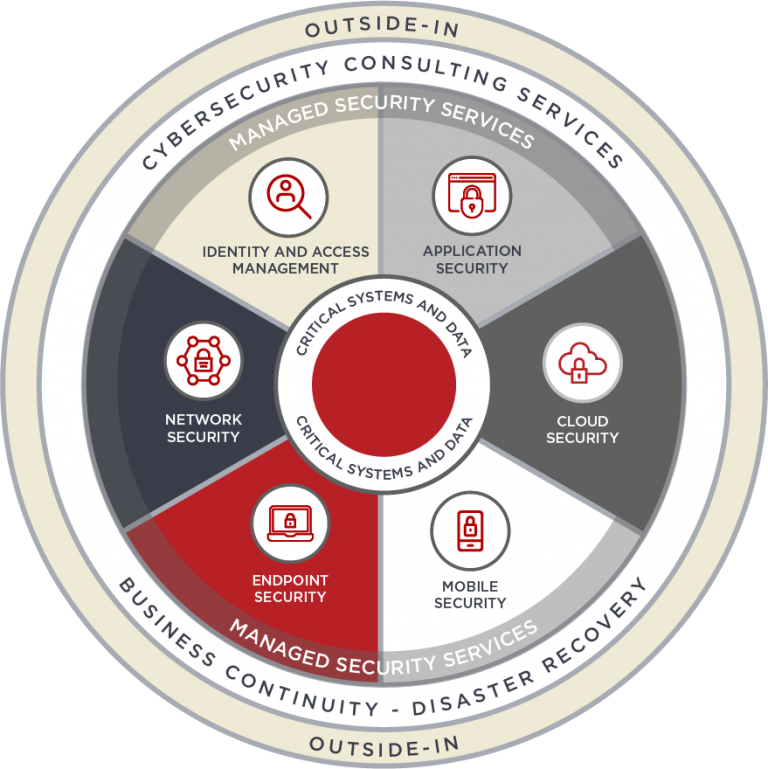
MobileCorp Managed Security service
MobileCorp utilises globally recognised security management tools and partnerships with leading security specialists to deliver its managed security service.
Services include:
- endpoint, network and cloud protection
- network monitoring
- adversarial security testing
- vulnerability scanning and analysis
- software updates and patching
- threat landscape visibility and intelligence
- threat and intrusion detection
- incident response
- predictive threat intelligence
- cloud security
- compliance reporting
- notifiable breach reporting management

Notifiable breach reporting management
Reporting notifiable breaches
In Australia, under the Notifiable Data Breach (NDB) scheme, companies who are bound by the Privacy Act 1988 are required by the government to report any instance of a data breach when personal information the organisation or agency holds is lost or subjected to unauthorised access or disclosure.
However, for most companies the first priority is to contain the breach and understand what’s happened. Often the right skills are not available to organisations internally for analysis and reporting of incidents, which is when having an MSSP like MobileCorp can greatly assist.
Incidents are not just ‘a ticket to close’
The days of a managed security service provider (MSSP) treating a customer incident as just another ticket are long gone… or rather they should be. Companies need MSSPs like MobileCorp who don’t just fix the issue quickly but also provide analysis and recommendations to prevent similar future threats.

Malware 101
Sometimes it’s good to remind ourselves just how real the threat is. Here is a list of all the different kinds of that malware can muck up a really good day.
- Virus: Like their biological namesakes, viruses attach themselves to clean files and infect other clean files. They can spread uncontrollably, damaging a system’s core functionality and deleting or corrupting files. They usually appear as an executable file (.exe).
- Trojans: This kind of malware disguises itself as legitimate software, or is hidden in legitimate software that has been tampered with. It tends to act discreetly and create back-doors in your security to let other malware in.
- Spyware: No surprise here – spyware is malware designed to spy on you. It hides in the background and takes notes on what you do online, including your passwords, credit card numbers, surfing habits, and more.
- Worms: Worms infect entire networks of devices, either local or across the internet, by using network interfaces. It uses each consecutively infected machine to infect others.
- Ransomware: This kind of malware typically locks down your computer and your files, and threatens to erase everything unless you pay a ransom.
- Adware: Though not always malicious in nature, aggressive advertising software can undermine your security just to serve you ads — which can give other malware an easy way in. Plus, let’s face it: pop-ups are really annoying.
- Botnets: Botnets are networks of infected computers that are made to work together under the control of an attacker.

Enterprise and governments are also getting caught out
While SMBs are an easy mark for malicious attacks, there have been plenty of enterprise and government organisations who have been caught out.
Here are some of the larger attacks on well-known companies:
- Optus September 2022: A cyber-attack on Optus resulted in the disclosure of up to 2.1 million customers' personal information including names, dates of birth, email addresses, driver's licences, Medicare cards and passport numbers.
- Medibank October 2022: Cyber criminals accessed the name, date of birth, address, phone number and email address for around 9.7 million current and former customers and some of their authorised representatives. This figure represents around 5.1 million Medibank customers, around 2.8 million ahm customers and around 1.8 million international customers.
- Canva May 2019: Canva revealed that a cyber-attacker had managed to access over 139 million users’ information, including names, email addresses, countries of residence, and cryptographically protected passwords. Canva managed to stop the attack midway, but it still urged users to change their passwords just to be on the safe side.
- Australian National University June 2019: ANU announced that it had detected an “unauthorised access to significant amounts” of data including the bank numbers, tax details, academic records and passport details of students and staff dating back almost two decades.
- Uber: In November 2017, Uber confirmed that it had lost the personal details of 600,000 drivers and customers in the United States. The company paid hackers $100,000 to delete the data and keep the breach quiet.
- Facebook April 2019: A digital media company called Cultura Colectiva based in Mexico left over 540 million records of user IDs, account names, likes, and comments exposed on a publicly accessible server. The Federal Trade Commission announced in June 2019 a $5 billion settlement with the company over its mishandling of user data. This follows on from March 2018 when the personal data of 50 million Facebook users was acquired by an external researcher who claimed to be collecting it for academic purposes but who passed it onto Cambridge Analytica, a company that served as Donald Trump’s data operations team during the 2016 election.
- Australian Red Cross Blood Service: Closer to home, in October 2016 the Australian Red Cross Blood Service ‘lost’ the private information of 550,00 blood donors from between 2010 and 2016. The data came from an online application form and included “personal details” and identifying information.
- Yahoo: Yahoo’s epic, historic data breach in 2013 compromised 3 billion people in total. The company revealed in 2017 that the accounts for every single customer during that time had been breached, including users of Tumblr and Flickr.

Learn more about 5G For Business
News and Insights from MobileCorp
Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now