- Home Page
- Managed ICT & IT Services
- Security Services
- Network Security Audit
Network Security Audit
The five most efficient cyber defenders are anticipation, education, detection, reaction and resilience
Stephane Nappo
Enquire Now
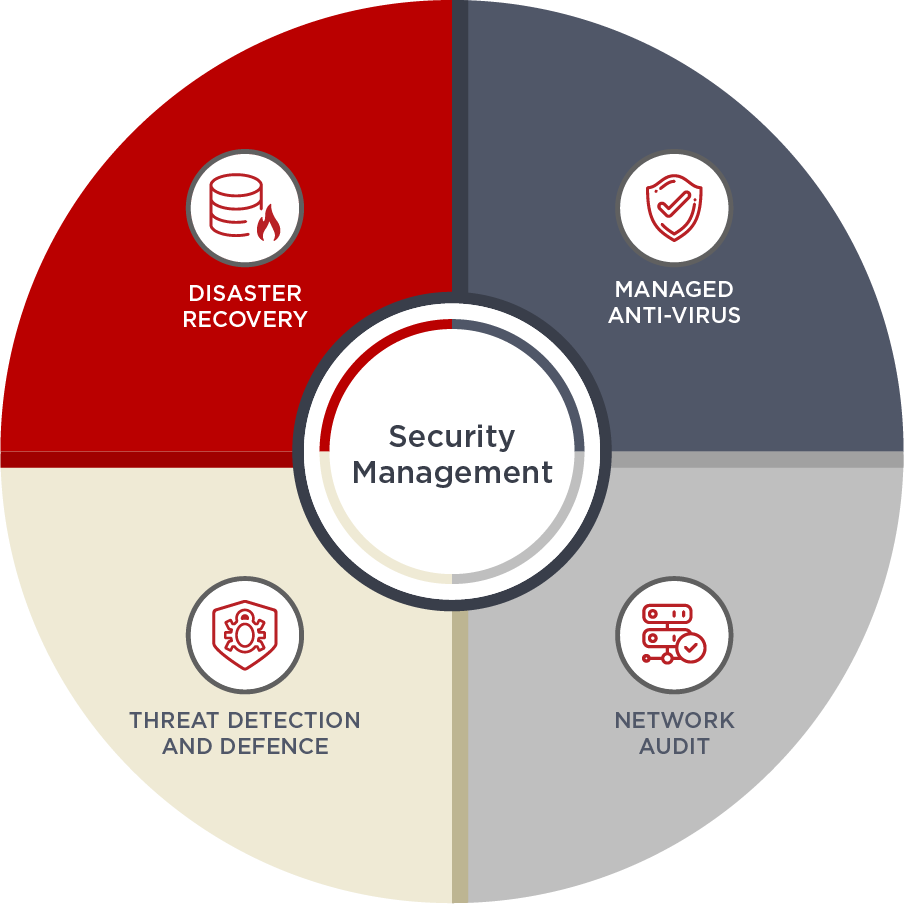



What is a Network Security Audit?
A security audit is a comprehensive review of existing policies, processes, equipment, and network infrastructure to probe for vulnerabilities and test for effectiveness.
It is one thing to have security measures in place, and another thing to validate their effectiveness in the face of an attack.
A key component of an audit is to test the environment to check for operational effectiveness.
A comprehensive audit report is prepared highlighting any areas of concern.
Security Audit goes further than IT Infrastructure
A thorough security audit will do more than assess the physical IT environment, it will also address the security culture in the business and identify internal control and regulatory deficiencies that could put the organisation at risk.
Due to the proliferation of wireless networks and mobile devices, through BYOD and IoT, the workplace has become a more agile and flexible environment. This has increased productivity and employee satisfaction, but also opened up a breeding ground for vulnerabilities and cyber risk.
Businesses that invest heavily in cybersecurity often base their investments on technology, but don’t sufficiently attend to the human side of it.
Both C-suite executives and policy makers rank ‘human error’ as the top cybersecurity risk for their organisation.

MobileCorp Security Audit
Outsourcing a security audit makes sense as it brings in security specialists with up-to-date expertise in identifying constantly emerging flaws and threats.
It also introduces an unbiased and objective perspective to the investigation.
However, a security audit does not have to be super complex or cost a fortune.
A 5-step audit covers all the bases for most companies.
Step 1. Scope The Security Perimeter
The first step in the auditing process is to clearly define the scope of the audit. For most companies this will include both managed and unmanaged devices and machines.
Managed devices will encompass a list of computers, machines, devices and databases that belong to the company directly, which contain sensitive company and customer data. Additionally, in a world that includes BYOD policies and IoT connected devices and machines, as well as contractors and visiting guests, the unmanaged segment of the audit should be positioned to continuously update visibility of all connected endpoints.
The security perimeter must include definitions relating to software that is allowed and not allowed to define a software perimeter. Finally, the scope should include all access layers: wired, wireless and VPN connections. In this manner, the scope of the audit will ultimately include all software and devices, in all locations, and ultimately define the security perimeter for the company.
Step 2. Define Threats
The next step is to list potential threats to the security perimeter. Common threats to include in this step would be:
- Malware – worms, Trojan horses, spyware and ransomware – the most popular form of threats to any organisation in the last few years.
- Employee exposure – making sure that employees in all locations change their passwords periodically and use a certain level of sophistication; (especially with sensitive company accounts) as well as protection against phishing attacks and scams.
- Malicious Insiders – once onboarding has taken place – employees, contractors and guests – there is the risk of theft or misuse of sensitive information.
- DDoS Attacks – Distributed Denial of Service attacks happen when multiple systems flood a targeted system such as a web server, overload it and destroy its functionality.
- BYOD, IoT – these devices tend to be somewhat easier to hack and therefore must be completely visible on the network.
- Physical breaches, natural disasters – less common but extremely harmful when they occur.
Step 3. Prioritise and Risk Score
There are many factors that go into setting priorities and risk scoring. Each item in the security perimeter needs to be ranked in order of impact that a loss of service would have on the business operations. Mapping out internal dependencies and potential alternative suppliers or staff that can be brought on if necessary, is essential to evaluate the most effective response in the face of a disaster.
Step 4. Assess The Current Security Posture | Testing
An assessment of the current infrastructure will highlight any existing vulnerabilities and the level of risk associated with each part of the enterprise network.
What redundancy failover process is currently in play? If a disaster occurs at the main business premises, how quickly can key systems be redirected to a hosted environment which allows the business to resume operations as quickly as possible?
Have all connected devices got the latest security patches?
What is the current firewall solution, threat detection, network monitoring, and response plan?
Testing the current security solutions will be part of this step.
Step 5. Formulate a Response and Remediation Plan
A security audit report will outline the scope of the audit and the outcomes observed. It will highlight vulnerabilities and threats. It will also make recommendations for actions to eliminate the risks identified.
The plan will not necessarily be confined to network or IT equipment. End user behaviour may be a potential threat and the response could involve additions to HR/IT policies and company-wide training.
Our Tech Partners
Leaders we are proud to partner with.





















Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now