- Home Page
- Mobility
- Mobile Security Solutions
- Mobile Threat Defence
Mobile Threat Defence
Security used to be an inconvenience sometimes.
Now it's a necessity all the time.
Enquire Now



MobileCorp Mobile Security Managed Service
MobileCorp offers a comprehensive Mobile Threat Defence managed service utilising market leading vendor, Jamf.
This can be deployed as a standalone solution - Jamf Endpoint Security.
It is also available as Telstra Enterprise Mobile Protect, powered by Jamf. TEMP can be procured and paid for on the Telstra Mobile bill. It may also be procured utilising Telstra loyalty funds. As the Telstra Mobility Partner of the Year 2023, MobileCorp is your leading Telstra partner for mobile security solutions.
MobileCorp also offers Mobile Security solutions bundled with a Unified Endpoint Management product
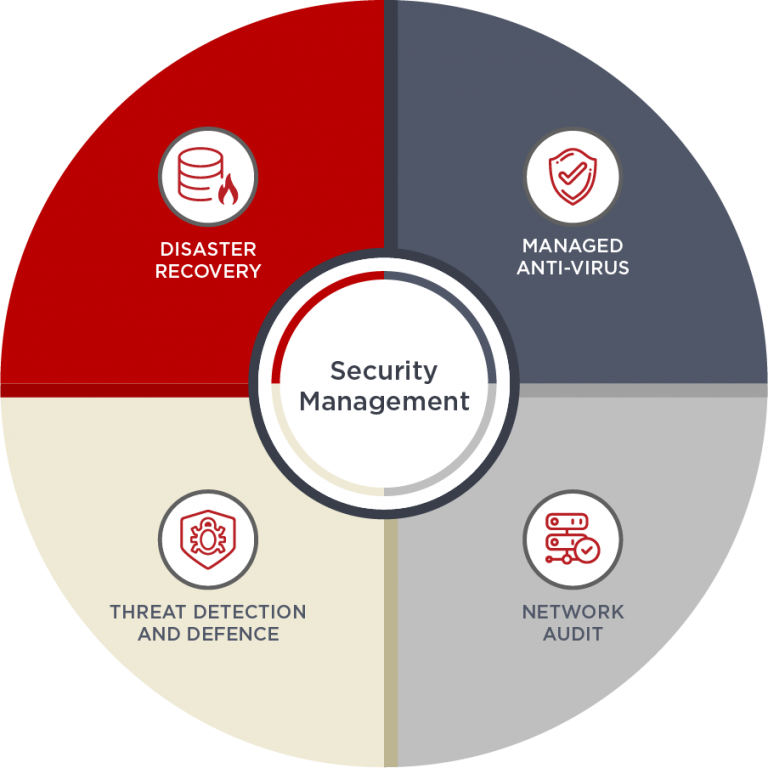
A mobile defence managed service by MobileCorp will provide:
- unprecedented visibility into business networks and systems
- predictive threat intelligence and analytics
- endpoint, asset, and network monitoring
- centralised alerts and threat management
- vulnerability management and reputation protection

Who needs MTD management?
Organisations of all sizes and across all industry verticals who wish to protect their corporate productivity and reputation would benefit from an MTD program, in addition to MDM or UEM.
High value use cases would include:
- enterprises in high-security verticals such as defence, government, emergency services
- enterprises in highly regulated verticals such as finance and healthcare
- organisations holding consumer data
- large Android device fleets
- companies with BYOD mobile fleets
What is the business case for MTD management?
There are several reasons why a company will decide to purchase an MTD solution. The most common business cases are:
Risk Management & Compliance
Sensitive Corporate Data
Mobile Endpoint Visibility
Without support for mobile devices, there is a gap left in the endpoint visibility picture. As mobile devices do not provide kernel-level access, the visibility is limited compared to what is available for Windows 10.
Unmanaged BYOD Devices
Companies with BYOD mobile fleets are particularly vulnerable especially where Microsoft Outlook app has been deployed as this is often a which is targeted to infect the infrastructure.
Our Tech Partners
Leaders we are proud to partner with.





















News and Insights from MobileCorp
Mobile Endpoint Security
Speak to our MobileCorp Representative
To get started with a technology solution, call us on 1800 243 252
Enquire Now